“The trillions of signals we analyse from our worldwide ecosystem of products and services reveal the ferocity, scope, and scale of digital threats across the globe.” Tom Burt
Corporate Vice President, Customer Security & Trust at Microsoft.
In this blog, we share our summary and some of the key findings from the Microsoft Digital Defense Report 2022 , exploring the current state of cyber security and actionable insights for your 2023 security roadmap.
A snapshot of our landscape
- Scope and scale of threat landscape: The volume of password attacks has risen to an estimated 921 attacks every second – a 74% increase in just one year.
- Dismantling cybercrime: To date, Microsoft removed more than 10,000 domains used by cybercriminals and 600 used by nation state actors.
- Addressing vulnerabilities: 93% of our ransomware incident response engagements revealed insufficient controls on privilege access and lateral movement.
Cybercriminals continue to act as sophisticated profit enterprises. Attackers are adapting and finding new ways to implement their techniques, increasing the complexity of how and where they host campaign operation infrastructure. Security is a key enabler of technological success. Innovation and enhanced productivity can only be achieved by introducing security measures that make organisations as resilient as possible against modern attacks.
The most effective defense against ransomware includes multifactor authentication, frequent security patches, and Zero Trust principles across network architecture.
Credential phishing schemes which indiscriminately target all inboxes are on the rise and business email compromise, including invoice fraud, poses a significant cybercrime risk for enterprises.
Ransomware

Contrary to how ransomware is sometimes portrayed in the media, it is rare for a single ransomware variant to be managed by one end-to-end “ransomware gang.” Instead, there are separate entities that build malware, gain access to victims, deploy ransomware, and handle extortion negotiations.
All human-operated ransomware campaigns share common dependencies on security weaknesses. Specifically, attackers usually take advantage of an organisation’s poor cyber hygiene, which often includes infrequent patching and failure to implement multifactor authentication (MFA).
Ransomware attackers are motivated by easy profits, so adding to their cost via security hardening is key in disrupting the cybercriminal economy.
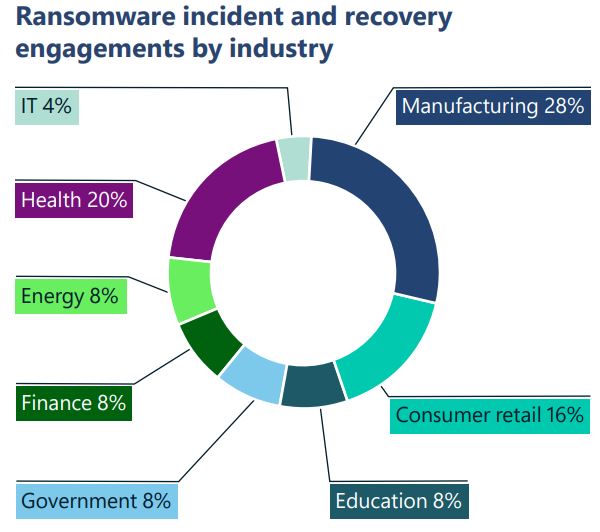
The three main contributing factors seen in Microsoft’s onsite response engagements:
- Weak identity controls: Credential theft attacks remain one of the top contributing factors.
- Ineffective security operations: Processes do not just present a window of opportunity for attackers but significantly impact the time to recover.
- Data protection strategy: Eventually it boils down to data—organisations struggle to implement an effective data protection strategy which aligns with their business needs.
Devices and Infrastructure
The pandemic, coupled with rapid adoption of internet facing devices of all kinds as a component of accelerating digital transformation, has greatly increased the attack surface of the digital world. Attacks against remote management devices are on the rise, with more than 100 million attacks observed in May of 2022—a five-fold increase in the past year. From a security operation standpoint, network defenders take multiple approaches to improving their organisation’s IoT/OT security posture. One approach is to implement continuous monitoring of IoT and OT devices. Another is to “shift-left”—meaning to demand and implement better cybersecurity practices for the IoT and OT devices themselves. A third approach is to implement a security monitoring solution which spans both IT and OT networks. This holistic approach has the significant added benefit of contributing to critical organisational processes, such as “breaking the silos” between OT and IT, which in turn enables the organisation to reach an enhanced security posture while meeting business objectives.
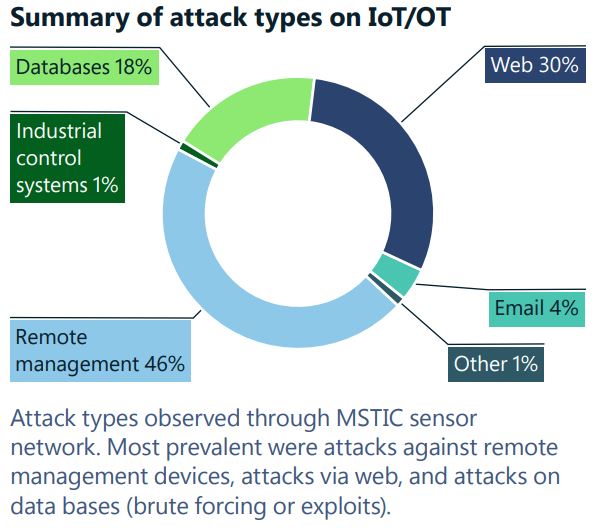
Cyber Resilience
Cyber resiliency is the ability of an enterprise to continue operations and sustain growth acceleration despite disruptions, including cyberattacks. The revolution in digital technology has seen organisations transform to become ever more connected in both the way they operate and the services they offer. As threats in the cyber landscape increase, building cyber resilience into the fabric of the organisation is as crucial as financial and operational resilience. This past year, threat actors continued to take advantage of vulnerabilities exposed during the pandemic and the shift to a hybrid work environment. The vast majority of successful cyberattacks could be prevented by using basic security hygiene. Modernised systems and architecture are important for managing threats in a hyperconnected world. Cyber security is a key enabler of technological success. Innovation and enhanced productivity can only be achieved by introducing security measures that make organisations as resilient as possible against modern attacks.
As we develop new capabilities for a hyperconnected world, we must manage the threats posed by legacy systems and software. This risk exposure is reinforced by the findings of the Microsoft Security Services for Incident Response team, a group of security professionals that helps customers respond to and recover from attacks.
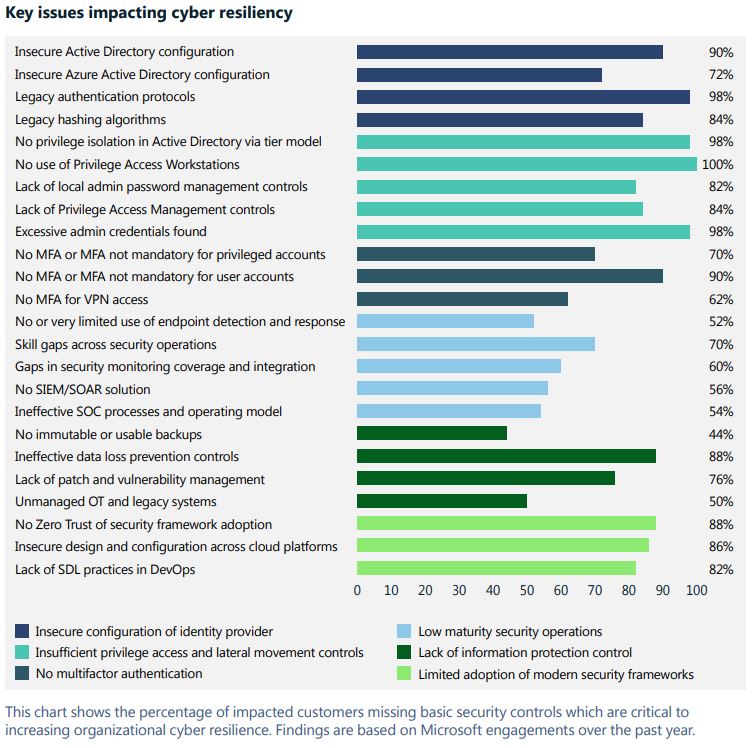
Actionable insights:
- Ensure all the accounts across your organisation are protected by strong authentication measures.
- Passwordless authentication offers the most secure and user -friendly experience, eliminating the risk of password attacks.
- Disable legacy authentication across your entire organisation.
- Protect high value and administrative accounts with phish -resistant forms of strong authentication.
- Modernise from an on -premises identity provider to a cloud identity provider and connect all your apps to the cloud -based identity provider for consistent user experience and security.
Addressing the human factor is also a key component of any cybersecurity skilling strategy. According to a Kaspersky Human Factor in IT Security study, 46 percent of cybersecurity incidents involve careless or uniformed staff who inadvertently facilitate the attack.
Next steps
As trusted Microsoft Partner, ActionPoint has had the privilege of working with many organisations to establish a security structure that protects their business. Let 2023 be the year of Digital Defense for yours. If you are looking for a trusted security partner, contact us today by emailing getstarted@actionpoint.ie.












